How secure is your business?
Find out how well your website protects sensitive data, online transactions and your business reputation.
Find out how well your website protects sensitive data, online transactions and your business reputation.
Protecting sensitive data is the end goal of almost all IT security measures. Two strong arguments for protecting sensitive data are to avoid identity theft and to protect privacy. The more valuable the information in your database, the more likely it is to be targeted. If your records include sensitive or financial information that could facilitate fraud, your database will be more appealing to hackers who can use or sell this information for financial gain.
Insecure server configuration and other known security vulnerabilities could potentially lead to financial loss arising from theft of corporate and financial information, theft of money, disruption to trading, loss of business or contract. As a way of protecting consumers against this kind of risk, ecommerce and other websites that collect customer credit and payments must be PCI DSS (Payment Card Industry Data Security Standard) compliant.
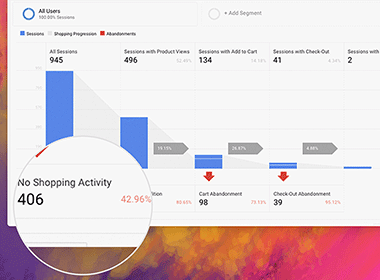
Your brand is the foundation of your business. It doesn't matter if you are a small business, corporation or something in between, a successful cyber attack can cause major damage to your business reputation and consumer trust. As a result, this could potentially lead to loss of customers, loss of sales and reduction in profits. Reputational damage can even impact on your suppliers, or affect relationships you may have with partners, investors and other third parties vested in your business.
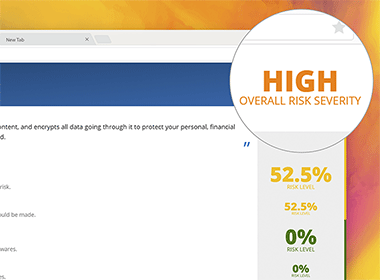
If your website has vulnerabilities, it is increasingly likely they will be identified and exploited by hackers. Thinking about the worst things that could happen to your business can help you deal with smaller risks. Risk evaluation allows you to determine the importance of potential risks to your online business. You can then decide to accept the specific risk or take action to prevent or minimize it.
Keep your business moving and keep your information safe.

The main target of security is not only creating rules but also following them.